Ta strona dostępna jest w języku polskim
There were requests for a more detailed description of how blockchain works and whether you can trust the technical solutions used to build the blockchain.
In this part I will present the cryptographic security of the blockchain, in the next part I will describe in detail the basic concepts of the blockchain and finally I will combine everything into a whole.
Cryptographic security
As I wrote earlier, one of the most important features of the blockchain is immutability, understood as the impossibility of removing and changing accepted and added to the chain of transactions.
This time I will try to describe the principles of the blockchain in a more technical way, for people who did not feel the strength of the solutions used in this technology to ensure permanence.
In fact, the matter is very simple and the whole security of the blockchain is based on three cryptographic components that have been known for many years:
- Digital fingerprint
- Merkle’s tree.
- Cryptography of the public key (asymmetric)
Digital fingerprint
This is also known as a shortcut or hash function. The Ethereum uses the Keccak-256 algorithm (instead of the popular and standardized SHA-3 algorithm, the lack of a standard algorithm is a conscious and deliberate decision of the creators of this platform).
The shortcut function works in such a way that after entering data of any size on its input, the output gets the input data shortcut always of a constant length (depending on the algorithm used, usually from 128 to 512 bits). The shortcut function does not require a key.
Digital fingerprint is most commonly used for:
- Maintain data integrity
- Pseudo-random number generators
- Storage of passwords
The characteristics of this mechanism:
- Unidirectional (irreversible). It is not possible to discover the source on the basis of which the imprint was created.
- Result always constant size
- Deterministic. For the same input data it returns ALWAYS the same abbreviation.
- Collision-resistant. It is very unlikely that two identical shortcuts will be created for different input data. The probability is the lower the greater the size of the abbreviation.
- No correlation with data. The algorithm creating the abbreviation causes the so-called avalanche effect. It consists in the fact that a change of one character in the input data changes the whole abbreviation (regardless of the location of this change – the beginning, the end of the data).
- Easy to calculate. Algorithms forming fingerprints are very effective, so they are used successfully in high-performance IT systems.
In a blockchain, the shortcut function is used to take care of data integrity and is the main component of the Proof of Work (PoW) mechanism.
Merkle’s tree.
The Merkle tree is a binary tree of abbreviations that stores transaction abbreviations in its leaves.
A feature of the Merkle tree is the safe and efficient validation of large datasets.
The following is a model of the Merkle tree
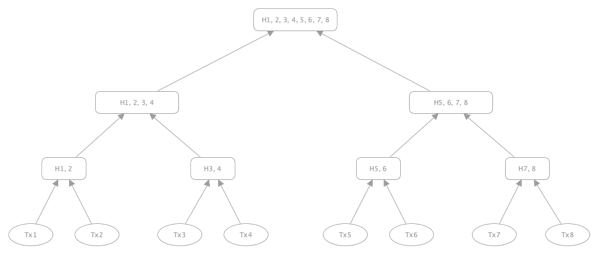
Fig.1 Merkle tree
How is the root of the Merkle tree created?
- We start from the bottom of the tree.
- First we count the abbreviation for the transaction Tx1 H1 = hash(Tx1)
- Then we count the digest for Tx2 transactions H2 = hash(Tx2)
- If we already have two shortcuts, we set a shortcut for their sum H12 = hash(H1 + H2)
- The same applies to the other branches of the tree until the root (root) is reached.
Such a mechanism causes that even a small change in any transaction will generate a new completely unique root shortcut. The comparison of root acronyms enables quick verification whether the transactions in the trees are identical.
The Ethereum uses a compressed Merkle tree variety (Patricia Merkle Tree).
Cryptography of the public key
Otherwise known as asymmetrical cryptography. The mechanism is that the key to encrypt the data is different from the key to decrypt it.
There are two elements here:
- Private keys. It is used to sign transactions and to decrypt data. No one is allowed to share it with anyone. A private key can be secured with a password required for its use.
- The public key. It is used to verify the signature of the sender of the transaction and to encrypt data. The name of the key indicates that it is publicly available and can be used by anyone who has access to it. This key is not password-protected.
The cryptography of the public key makes it possible:
- Sender’s verification
- Transaction security (only the recipient and the sender can read the content)
How does asymmetric cryptography work?
Let us consider two scenarios: signing transactions and data encryption.
Signing of transactions
- The sender creates a non-confidential text (e.g. the content of a document)
- The sender signs the non-confidential text with his private key
- After signing the signature, a plain text digital print is created, which takes into account the private key.
- The recipient receives a non-confidential text and a digital imprint
- The recipient uses the public sender’s key to verify a digital print attached to a non-confidential text
- The consignee shall be informed whether the signature originates from the sender
Data encryption
- The sender creates a non-confidential text (as above)
- The sender encrypts the plain text with the recipient’s public key
- The recipient receives an encrypted text
- The recipient decrypts the text with his or her private key
- Recipient sees a non-confidential text
Analyzing the above scenarios we can create another more complicated one, in which the text will be encrypted with the recipient’s public key and signed with the sender’s private key. Then, after reaching the recipient, the signature is verified with the public key of the sender and then decrypted with the private key of the recipient.
The Ethereum uses the Elliptic Curve Cryptography (ECC) algorithm for public key cryptography. The feature of this algorithm is to provide a high level of security with a key shorter than e.g. in the RSA algorithm.
Summary
It seems to me that now you have much more certainty about the safety mechanisms used in the blockchain. Even minor and potentially harmless changes in trades will be revealed immediately, so you can rest assured about the data in the blockchain. They will be introduced once and for all.
The cryptography of the public key in the blockchain makes it possible to determine:
- Proof of authenticity
- Proof of identity
- Proof of ownership
If you have any questions, please do not hesitate to contact me.

0 Comments Leave a comment